The Internet of Things (IoT) is one of the fastest growing areas of technology on the planet. In a digitally transformed world, people are using IoT connected devices for more and more services; from healthcare, to personal finance and the monitoring of utility consumption.
Virtually every aspect of life is being enhanced with the help of applications running in every device, all connected in the Internet of Things. Vacuum cleaners, cars, lights, kettles and fridges are all getting an internet connection and a processor to run applications. .
While providing a smooth and convenient customer experience, one wonders about the security implications of these devices. As with almost all emerging technologies, there comes an associated cybersecurity risk raising the need for security to the edge.
The recent 2020 Unit 42 IoT Threat Report found that the general security posture of IoT devices is declining, leaving organisations vulnerable to new IoT-targeted malware as well as older attack techniques that IT teams have long forgotten. IoT devices are perceived as a low hanging fruit by attackers, and their vulnerability makes them easy targets which are often used as a steppingstone to attack other systems on the network.
What if one of your IoT device is hacked? It opens a door to all your devices connected to the internet, collecting data and communicating with each other. Even the simplest and least expensive IoT device needs to have the highest level of security and trust.
25 billion
IoT devices today, with 50 billion predicted by 2030
98%
of all IoT device traffic is unencrypted
IoT devices require the collection and transmission of a large amount of sensitive information such as personal health and financial data. They also include digital identification and use security algorithms to generate keys to encrypt clients’ data securely. Transmissions and data are normally protected by cryptographic algorithms using random numbers for encryption, digital signing, and hashing – the basic cryptographic implementations that protect everything digital.
Encryption keys are comprised of random numbers that should be impossible to predict or decipher. The strength of protection afforded by cryptographic encryption is dependent on the degree of randomness and unpredictability used to create the encryption key. The greater the degree of randomness, the better protected information will be.
Some types of standard encryption are vulnerable to hackers who can create their own algorithms to unlock the encryption key. Many IoT devices have random number generators (RNG)embedded already, used for applications security, and for transmission security; however, these do not always offer ‘true’ randomness. Quantum random number generators (QRNGs) offer a greater degree of randomness while also being invulnerable to environmental perturbations and allowing live status verification.
As digitization continues to encompass every aspect of our lives and work, security challenges are evolving to the quantum level. Quantum Random Number Generation is the most reliable source of entropy, delivering a more secure method of generating encryption keys for the quantum era.
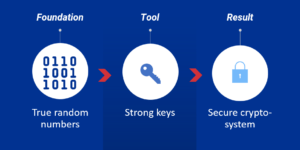
Quantum randomness generates the strongest keys, providing the highest level of trust.
ID Quantique recently launched its true Quantum Random Number Generator (QRNG) Chip, offering the highest achievable robustness and security for the creation of random bits. The chip’s compact size and resistance to external environmental perturbations make it ideal for use in IoT, mobile phones, V2X automotive, computing, critical infrastructure and security applications.Three models of IDQ’s QRNG chip are available, offering a range of size, performance, power consumption and certifications designed to meet various industry-specific needs.
The first miniaturized Quantum Random Number Generator, Quantis QRNG IDQ250C2 is designed and manufactured specifically for IoT, mobile handsets and edge devices. Its low profile, compact size and low power consumption, is ideal for securing the collection and transfer of sensitive data at the edge.
ID Quantique and SK Telecom recently announced the world’s first QRNG chipset equipped 5G smartphone.The integrated Quantum Random Number Generator (QRNG) in the Samsung Galaxy A Quantum applies quantum technology to smartphone security, enabling SK Telecom to provide the highest level of trust for customer’s sensitive information.
IDQ’s quantum technology delivers the most secure encryption keys available today and is designed to meet the security requirements of the quantum computing era, meaning your customers can be assured of the highest level of security.
In the hyper-connected 5G era, where 43 billion devices are expected to be connected through wireless networks in 2026, the importance of cybersecurity to the edge rises exponentially. IoT and edge devices are now connecting home, hospitals, factories, infrastructure, schools and shopping locations, requiring the collection and transmission of more and more sensitive data including financial, health, business and personal information, which raises the need for security to the edge.
The risk to IoT security is already real and steadily increasing. Security has not necessarily been a focus point when launching an IoT device on the market, mostly because of cost and integration barriers. These can be mitigated today, and organizations can now differentiate themselves while protecting their investment with top end future-proof quantum security.