Today, we are reaching a paradigm shift: the quantum threat forces us to fundamentally rethink our cryptography. Increased geopolitical and commercial pressure, technological advancements and malicious actors are putting our data confidentiality and sovereignty at risk.
In a world where the quantum threat will render current public key cryptography obsolete, and bring long-term uncertainty to the next generation of post-quantum algorithms, we leverage quantum technologies to protect data and communications, keeping society, businesses and people safe now and in the long-term future.


Internet will never be the same. A quantum computer’s ability to solve complex problems like factorization means that it will also have the power to break keys – the same keys that we rely on to protect our cryptographic systems.
In fact, quantum computers pose a very real threat to data security today. The long-term value of much of today’s data means it is vulnerable to a ‘download now, decrypt later’ attack, where cyber criminals steal data and store it for decryption when quantum computers become available.

As quantum computing matures, organizations must move towards a quantum-safe stance to protect themselves and ensure business continuity. This will likely require the adoption of multiple technologies and approaches.
Quantum Key Distribution and Quantum Random Number Generation provide the cornerstone of a long-term quantum-safe strategy.
Migrating to a quantum-secure stance is no trivial task. As the migration time is the only thing we control, it is crucial not to allow a lack of internal expertise and overwhelming complexity expose you to important liabilities.
Any cryptographic system is only as secure as the encryption keys it uses. The first step towards good data protection is therefore to start with good keys. The security of the keys is determined by the degree of randomness (entropy) used to generate them.
For a source of genuine and provable entropy, cryptographic systems are leveraging quantum random number generators, which rely on the non-deterministic character of quantum mechanics to generate entropy.
Simulate, design and build any kind of quantum-safe network to suit your needs.
Meet Clarion KX – IDQ’s extensive Key Exchange Service that brings the full scope of our quantum-safe solutions together to facilitate large-scale QKD deployments.
The software layer plays a critical role in holistic quantum cybersecurity ecosystems to guarantee end-to-end post-quantum data communication security.
Ensure easy integration with existing infrastructure, scalability, guaranteed governance and control.
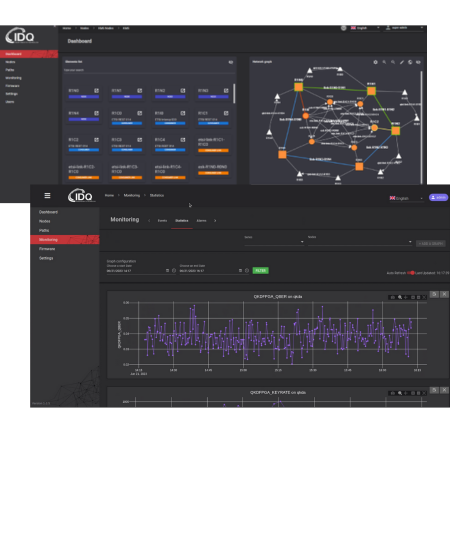
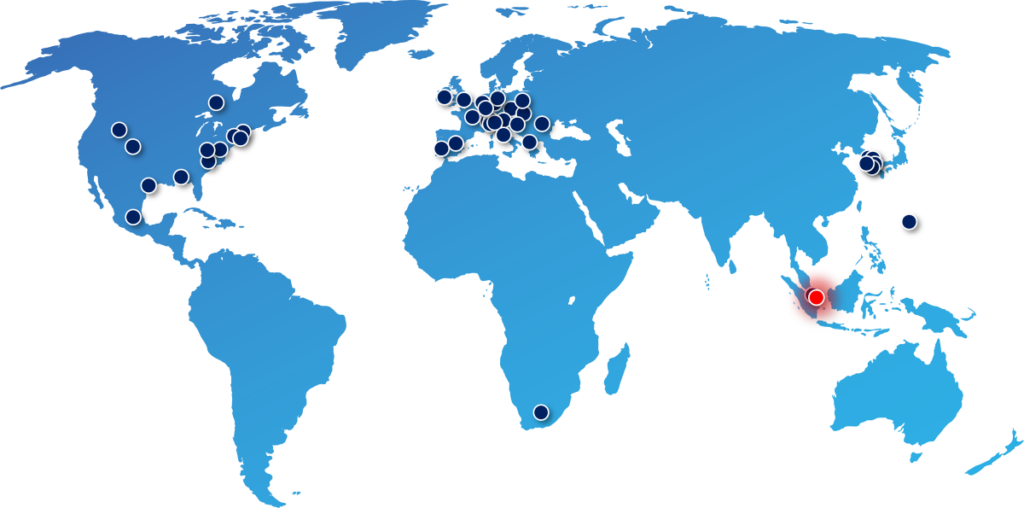
IDQ and Singtel partnered to build a Quantum-Safe Network in Singapore, developing use cases to drive adoption among organizations and enabling them to build trust with their customers.
> Read the use case
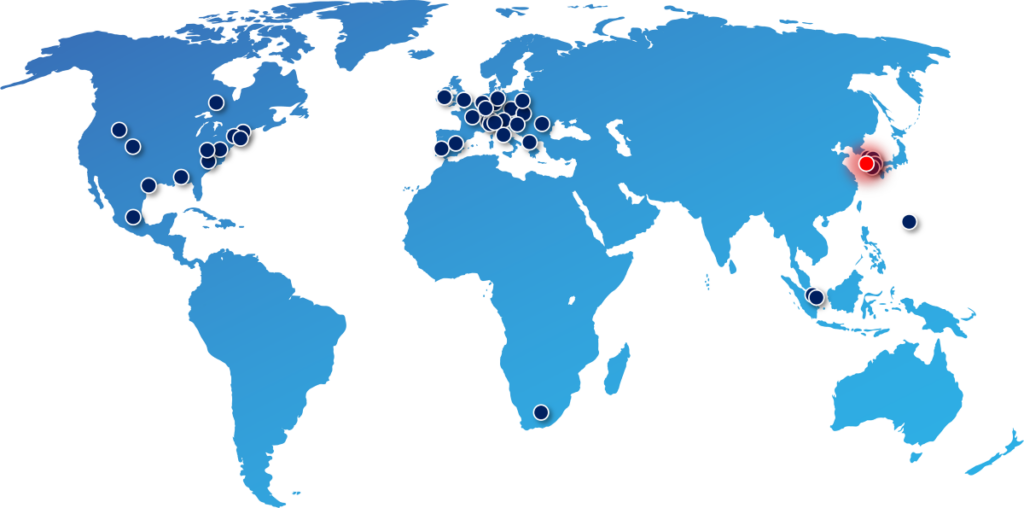
The largest and most sophisticated quantum-safe infrastructure on a national level outside China, combining 48 government departments over a single 800-km converged network.
> Read the use case
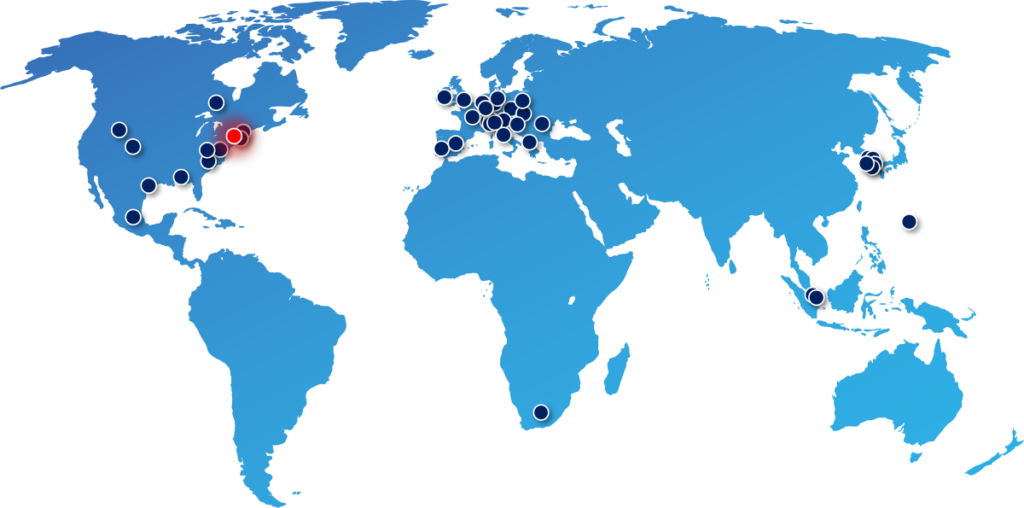
QKD is combined with classical cryptography to prevent “Harvest Now, Decrypt Later” threat and to guarantee long-term protection of sensitive financial data.
Securing control systems of remote power substations and power plants through both optical ground wire cables and aerial fibers, while maintaining performance despite environmental changes.
Securing an Institute of Health’s emergency communication network and protecting key data and personal information held by public institutions.
Building a 1770-km long intercity QKD infrastructure in Poland to provide a secure communication infrastructure for digital science, economy and social innovations.











