Today’s security infrastructure will not be fit for purpose in a post quantum computing world. Much of the cryptography we currently depend on for authentication, integrity and confidentiality of data is based on public key encryption algorithms. The exponential growth in computing power represented by quantum computers makes the mathematical problems used in the current public key schemes obsolete. To ensure long-term data protection, IT and communications network operators must adopt quantum-safe technologies as quickly as possible.
Quantum computing: an unprecedented threat
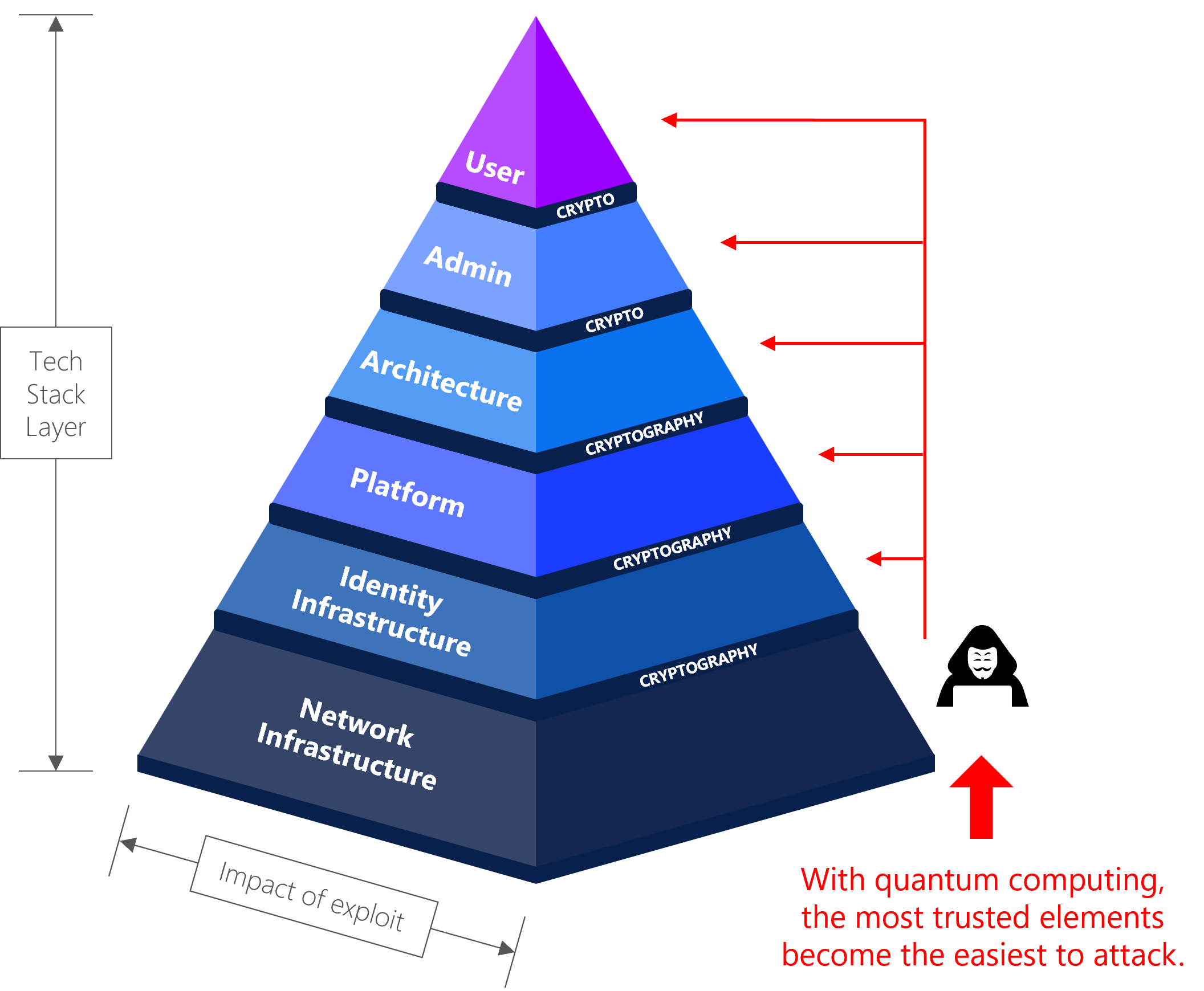
Today, both cryptography and other security systems are integrated throughout all layers of the technology stack. Most cyberattacks begin at the top of the stack, at the user level, requiring of the attacker to circumvent multiple layers of defense to gain access to the core systems that host valuable data.
The quantum threat inverts this process, allowing attackers to easily access the data at the bottom of the stack, by simply tapping the network infrastructure layer.
Although there are no cryptographically relevant quantum computers available right now, billions are being invested by government and commercial organizations across the globe in a race to be first to bring a quantum computer to market. However, this doesn’t mean today’s data is safe from the quantum threat.
Much of the data currently transmitted across private and public networks has long-term value. Commercially sensitive data, medical and financial records, IP and personally identifiable data can all be captured today and decrypted later. HNDL threat, thus, impacts the confidentiality of critical information during its lifetime.
In addition to data’s inherent value, it is often regulated by data retention policies that require to safeguard the data for its lifetime, which varies widely across industry sectors. “Harvest now, decrypt later” (HNDL) attack vector represents a very current threat to tomorrow’s data security. Any entity transferring data with long-term secrecy requirements should move to quantum-safe cryptography now.
Industry experts warn that a cryptographically relevant quantum computer, which could implement Shor’s algorithm with large enough data sets, will be available by the end of the decade. Since history has shown that cryptographic migrations are much more complex and lengthier than expected, the importance of mitigating the HNDL threat timely should not be underestimated.
It is worth recognizing that organizations can now leverage multiple cryptographic technologies to both lower the migration risks and costs, as well as to achieve long-term resilience against the rapidly emerging quantum threat. It is crucial not to allow a potential lack of internal expertise or the overwhelming complexity of migration to expose your organization to significant liabilities.
Implementing post-quantum cryptography won’t happen overnight
For many organizations, cryptography has been a blind spot as typically not managed as a strategic asset. Only now are many coming to grasp that cataloguing and triaging cryptography is difficult, time consuming and error prone. To identify all the types of risks they are potentially exposed to, organizations will need to decide how to mitigate the impact: what can be avoided, what can be reduced, what can be insured against, and what will just have to be accepted as a residual risk.
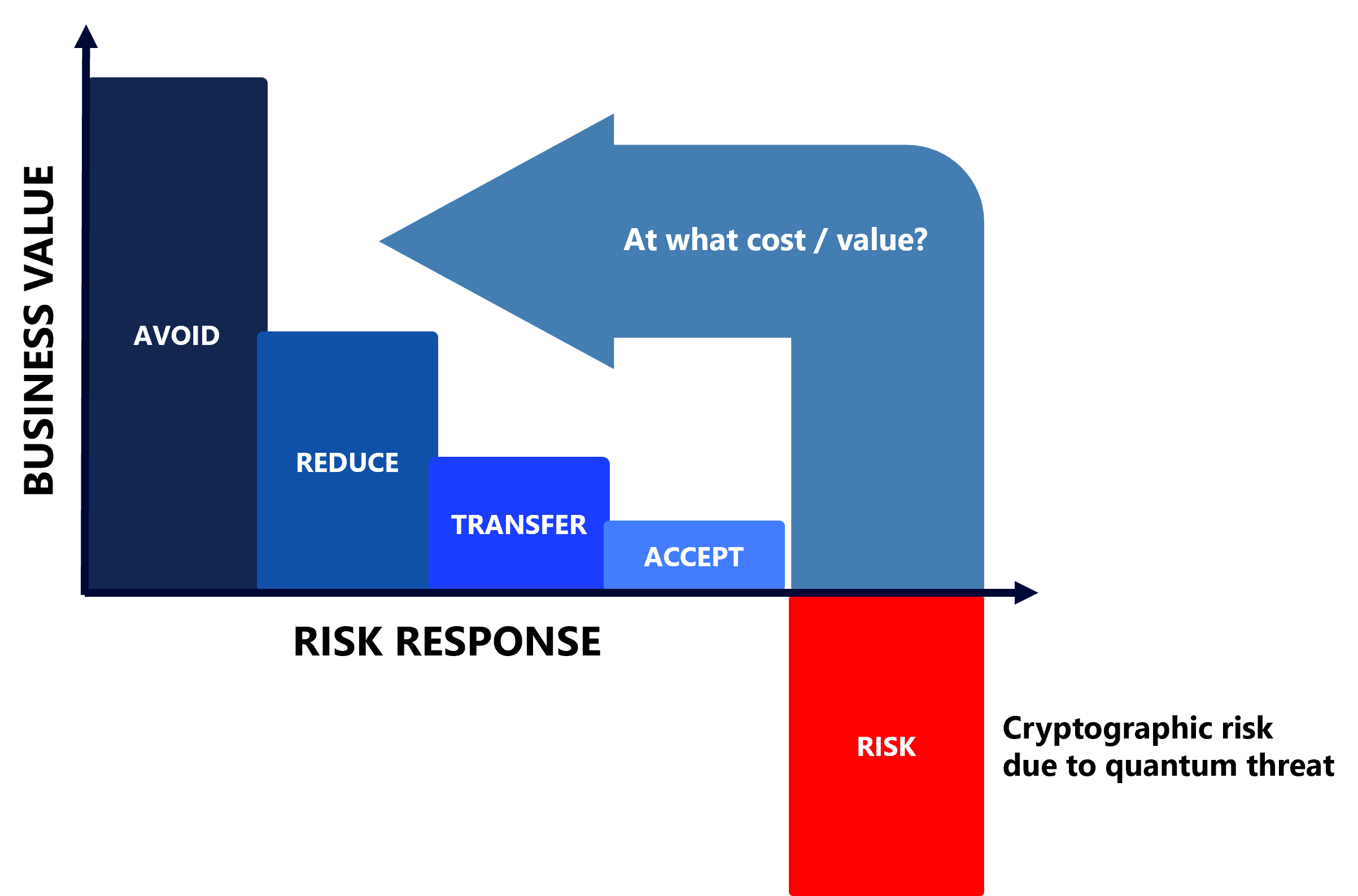
Upgrading infrastructure will require greater visibility of how and where cryptography is currently being used and legacy systems will need to be upgraded or replaced entirely. The process of identifying and documenting every instance of cryptography, every library, and every certificate will be time-consuming, complex, and expensive, which means the timelines for migration will vary significantly between assets.
This is just the first step in a process that will require ongoing auditing, risk assessment, road mapping and potentially, perpetual upgrading of systems with every upcoming standard. For many entities, this process is expected to take a decade or more, moving the migration timeline beyond the acceptable risk to confidential assets and well into the quantum threat horizon.
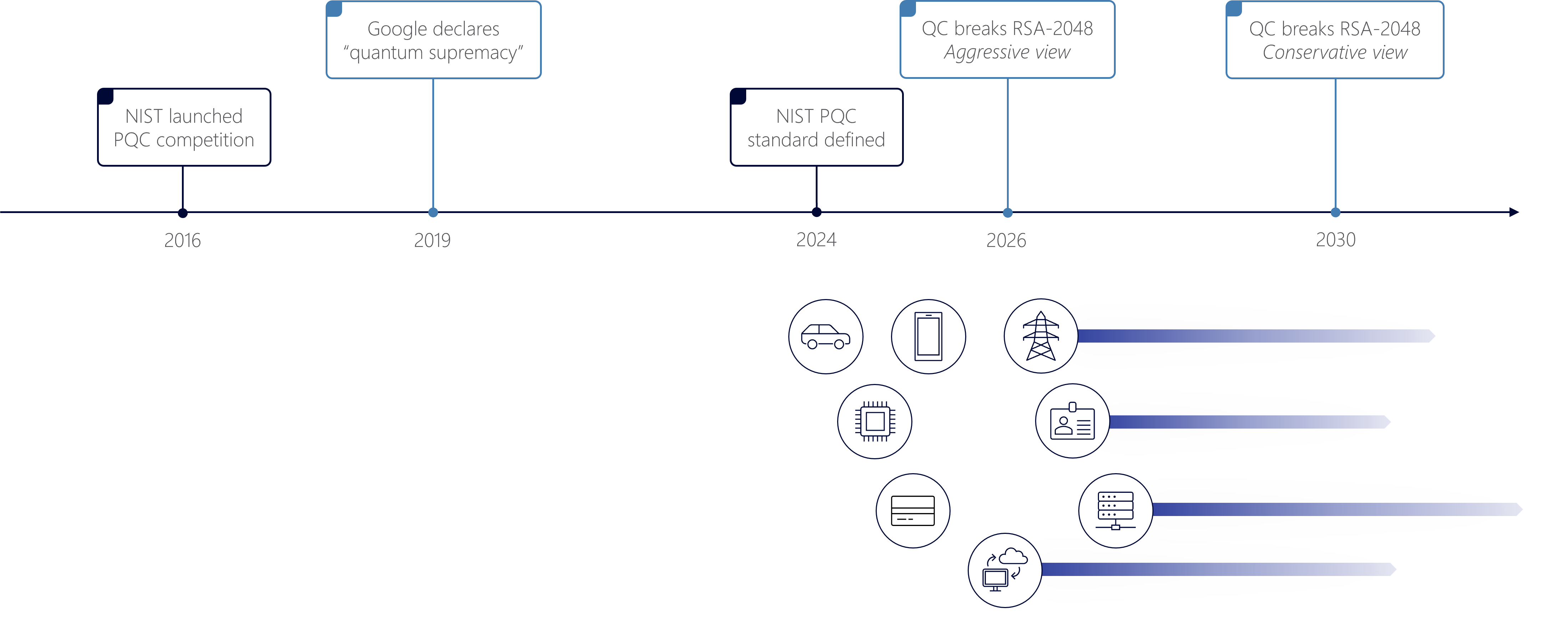
The journey to quantum safe infrastructure is likely to be long, complex and expensive. Most concerning of all, there is a great likelihood that the migration will need to be repeated with the release of newer standards, often before it is complete. Putting it off will only expose your organization to greater risk, so the time to start is now.
To mitigate the risks and safeguard information in the quantum era, a hybrid cybersecurity approach that integrates Quantum Key Distribution (QKD), Post-Quantum Cryptography (PQC), Quantum Random Number Generators (QRNG), and Quantum Key Management Systems (Q-KMS) is being embraced by the experts.
Their integration creates a cohesive, robust, multi-layered security framework that leverages the strengths of each technology and provides for defense-in-depth. This hybrid approach ensures that organizations can protect sensitive information against current threats while preparing for the quantum future.
Two main tools emerge as solutions to tomorrow’s secure infrastructure: Post-Quantum Cryptography (PQC) and Quantum Key Distribution (QKD).
Public key infrastructures that secure the Internet and corporate systems will transition to newly standardized PQC algorithms over the next few decades. Until the security of a particular generation of PQC is proven, these algorithms will often operate in a hybrid mode alongside today’s classical ECC and RSA algorithms. Where long-term confidentiality and high-assurance security are needed, as well a greater level of flexibility for PQC migration, QKD infrastructure can be used to ensure data protection. By employing a defense-in-depth approach with QKD at the core of the network and PQC extending security to the edge or protecting the application layer communication, the attack surface is significantly reduced, enhancing overall network security and enabling a zero-trust architecture.
Given the complementary aspects of PQC and QKD, a combined solution offers more robust protection, especially when it is combined with pre-shared keys and symmetric cryptography. This approach ensures no single point of failure can compromise the entire system.
While large organisations can embark on such solution supported by their large budgets, mid-size organizations can work with their telecom operators to benefit from it with minimal investment. For cloud and telecommunications service providers, offering Quantum-Safe as part of their services can also represent a strong point of differentiation that will appeal to customers seeking seamless and cost-efficient “secure by design” solutions.
Hybridization is crucial for ensuring long-term data security and serves as a cost-effective migration strategy, managing risk, migration time, and costs efficiency. The migration to quantum-safe communication can be significantly derisked and accelerated with the appropriate use of cryptographic hybridization and crypto-agile solutions. IDQ’s Quantum Key Exchange platform, Clarion KX, is purpose built to support large and flexible deployments of QKD and PQC, providing a high degree of flexibility, cost efficiency of scaling and high SLAs.
Need help planning your migration to quantum safe?