Quantum computer ready, set, go!
Cybersecurity is rapidly approaching a tipping point. The anticipated availability of quantum computers will render the public key infrastructure we currently rely on to secure our digital landscape obsolete. Without action, forget about your secrets, say goodbye to your competitive advantage, and prepare yourself to narrate the sweet memories of what privacy was to your grandchildren. We need to start revamping our cybersecurity infrastructure today and make it resilient against quantum computer attacks. This is known as Quantum-Safe security.
Why quantum?
As computers became more powerful, and able to crack current encryption defences, the answer was often to make the maths harder by making encryption keys longer. That’s fine if we’re talking about a classical computer – factoring an RSA 2048bit encryption key would take so long as to be practically impossible. However, quantum computers don’t just move the goal posts, they throw them away and start playing a different game entirely.
Quantum advantage (the point at which a quantum computer can solve a problem that is mathematically near impossible for a classical computer) was first achieved in 2019.
Since then, the cybersecurity industry has not been sitting idle. Progress towards quantum-safe security has been steady in two different fields. First, there has been significant investment in the field of post-quantum cryptography. New quantum-resistant algorithms are being developed, in particular by the National Institute of Standards and Technology (NIST). Second, in an interesting twist, quantum technologies themselves are called to the rescue against quantum computer associated threats. Today, we can already rely on some well-established ones, like Quantum Random Number Generation and Quantum Key Distribution. In the future, the Quantum Internet will offer perfectly secure key distribution on a global scale, amongst other things.
Why now?
Changing cryptographic systems is not straightforward. It doesn’t happen overnight, so organisations across the world are being encouraged to act now to ease the transition in the future. One of the challenges facing any fundamental change in cryptographic primitives is establishing a set of standards. The NIST began this program in 2016. Mid-2020 NIST announced the third-round candidates and final standards are expected in 2024.
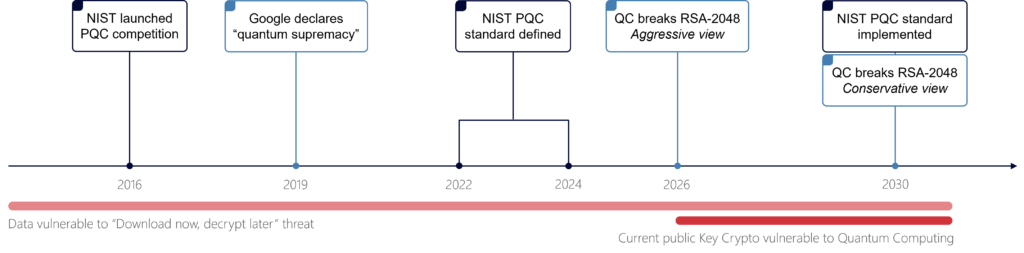
In 2021 NIST published “Getting ready for post-quantum cryptography”, in which they acknowledge that the implementation of standards could take anywhere from 5 to 15 years. Given that experts estimate a viable quantum computer could crack RSA 2048 within a 5 to 10-year time frame, this leaves the industry with a significant corridor of uncertainty.
EXTRACT FROM NIST PUBLICATION
“We cannot accurately predict when a quantum computer capable of executing Shor’s algorithm will be available to adversaries, but we need to be prepared for it as many years in advance as is practical. As previously stated, when that day comes, all secret and private keys that are protected using the current public-key algorithms—and all available information protected under those keys—will be subject to exposure. We need to determine where, why, and with what priority vulnerable public-key algorithms will need to be replaced, and we need to understand the constraints that apply to specific use cases. These initial steps in developing and implementing algorithm migration playbooks can and should begin immediately.”
A good starting point to assess where you stand is to use Michele Mosca’s theorem:
- X years: How long do you need encryption to be secure?
- Y years: How much time will it take to re-tool the existing infrastructure with large-scale quantum-safe solution?
- Z years: How long will it take for a large-scale quantum computer to be built?
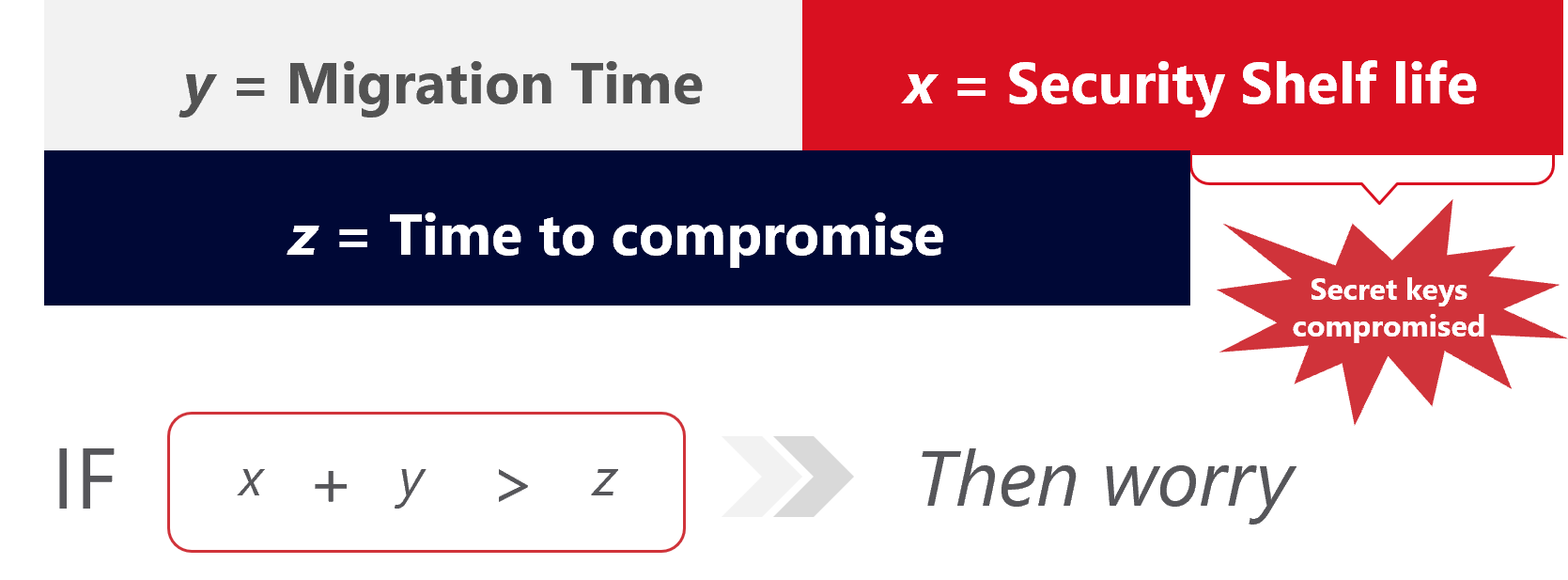
Let’s take an example: if your organization stores financial information such as customers’ bank account numbers, these are believed to have value of 10 or more years (X). If you estimate that upgrading to quantum cryptography will take three years (Y), and that a quantum computer attack able to break current public key crypto will be available in 7 years (Z), then your data will be exposed for six years if stolen.
This is without taking into account the “download now, crack later” threat, where patient hackers can harvest encrypted data today and decrypt it at a later date when the technology allows. This means cybersecurity professionals should not only be focussed on a roadmap for migration but on ensuring the confidentiality, authenticity and integrity of data today.
Quantum security
As with most complex security scenarios, there is no single solution. Different security challenges will require different approaches. QKD and post quantum cryptography (PQC) are not mutually exclusive technologies. The most secure future would feature a combination of both technologies.
Of course, the next generation of encryption algorithms should also come with a caveat. They are not a permanent cure. By its very nature, computational security comes with an expiry date. If I make a confidential transaction today, I must choose both the algorithm and the parameters, such as the key length. I make a bet that the algorithm itself and the key length I chose will remain safe despite future progress in attacks and in computer power. QKD, on the other hand, does not depend on future progress in computation: it offers genuine long-term security for key exchange, since it offers unhackable key distribution.
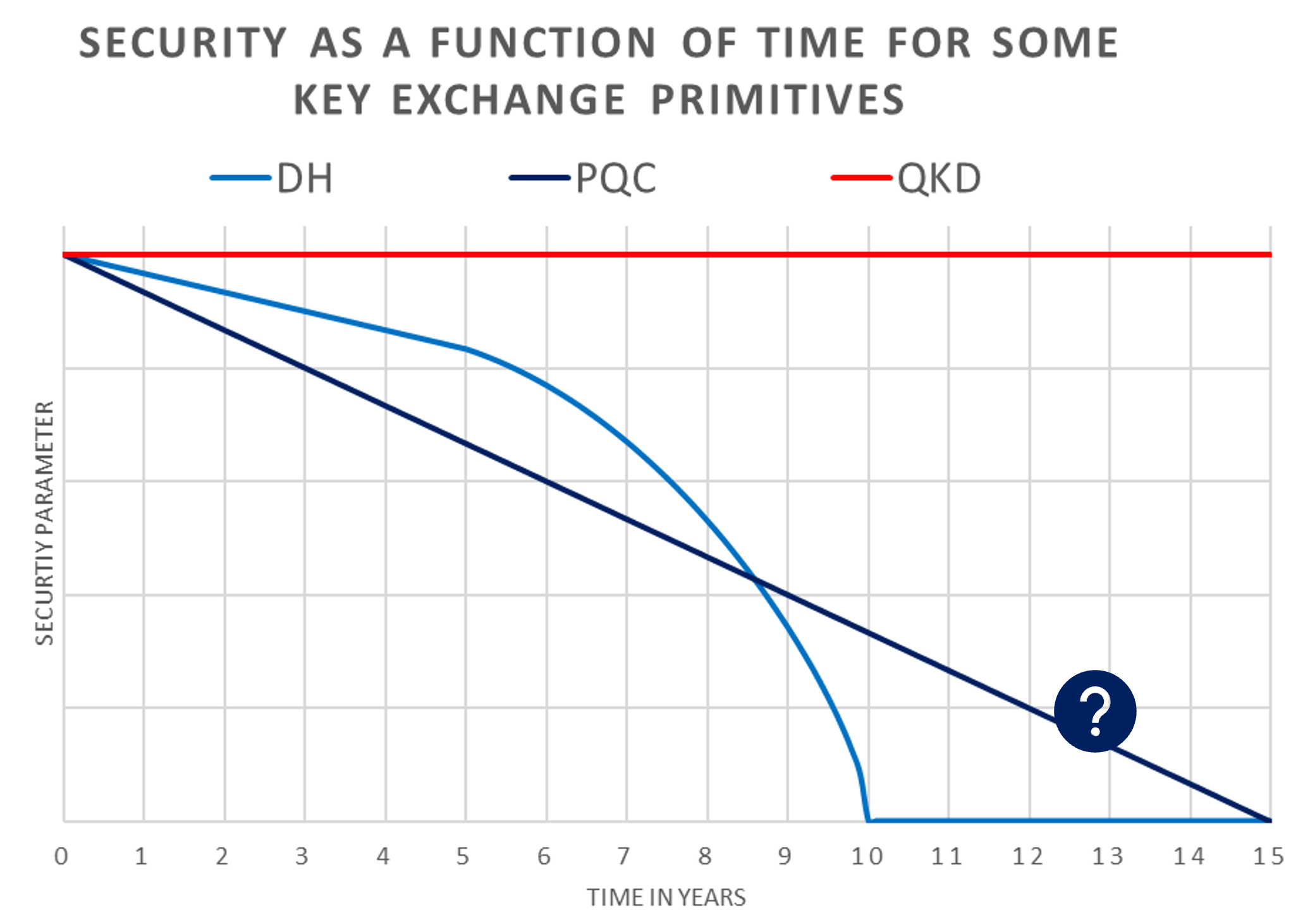
The bottom line is, as universal quantum computing is coming, it’s essential to act now. Do not wait until a perfect solution emerges… It is very likely that it will be too late.
- Want to get ahead of the quantum curve? Read this interesting article from Martijn Dekker, CISO at ABN AMRO: Why All CISOs Need to Prioritize Quantum Tech Today
- Interested to start your transition to Quantum Safe Communication? Feel free to contact us.


